The state of the world's workforce has changed—swiftly, significantly, and in ways that previously had been impossible to predict.
Many of the most notable transitions, such as the massive move toward flexible work and growing adoption of cloud services, are having a major impact on data security. From compromised endpoints to heightened hacking attempts, the sheer volume of data breach threats and challenges IT teams now face is staggering.
Here's a quick look at the biggest changes from the past year—and what they could mean for your organization moving forward.
Remote work is more prominent than ever.
After the world's largest work-from-home experiment in 2020, it appears remote work is here to stay.
According to the latest hybrid remote work stats from Gallagher, 86% of organizations plan to continue with flexible work-from-home arrangements long term.
WillisTowersWatson research shows the number of full-time remote employees is now three times higher than 2019 levels.
By the end of this year, Global Workplace Analytics expects 25% to 30% of the workforce to be working from home multiple days a week—approximately eight times higher than pre-pandemic estimates.
Additional surveys show that one in five employers have already implemented hybrid work, and that 20% of workdays will be done from home moving forward—up from just 5% before 2020.
As flexible work arrangements increase, so do data security risks.
Risky behaviors like password reuse and unsafe downloads have long plagued IT teams. And now, those security vulnerabilities are being magnified more than ever. In early 2020, when pandemic-related anxiety set the stage for “hacking mayhem,” cyberattacks of all sorts surfaced. Phishing scams, spyware, ransomware attacks, and malware successfully circulated at a time when cybercriminals were able to prey on fear and confusion about the virus.
Now that many people have settled into more permanent remote work setups, the focus has shifted to other corporate vulnerabilities. An estimated 53% of employees are using personal laptops for work, often with no new tools to secure them, and 45% haven't received any new security training.
As a result, many organizations face mounting concerns about the potential for data leakage, dangerous app downloads, and unsafe content.
According to the Ponemon Institute, 68% of organizations had already fallen victim to successful endpoint attacks in 2019. Then in 2020, as the number of remote workers reached an all-time high, more than half of surveyed IT professionals named endpoint security as their #1 challenge.
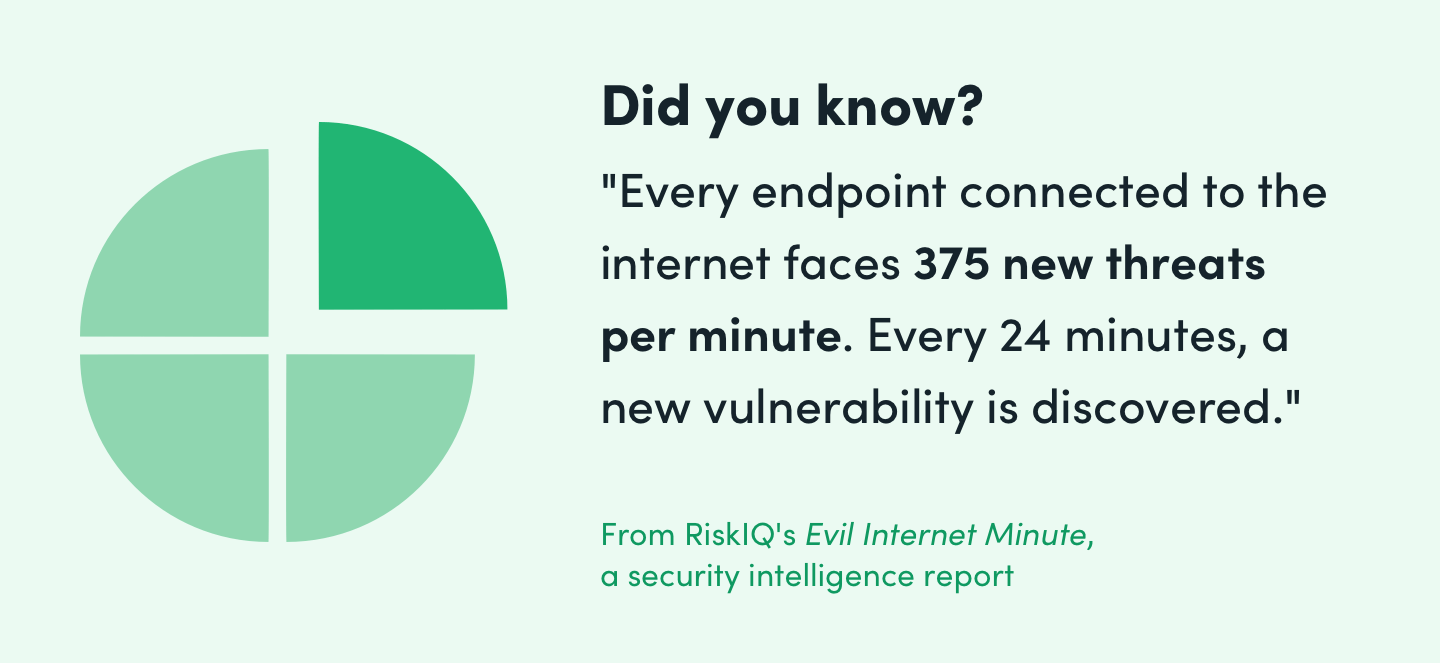
With so many people relying on personal devices to access corporate apps and data, the risks are significant: Once malware is successfully planted on an unmanaged laptop, tablet, or smartphone, it can potentially infect the entire corporate network. And according to one recent assessment from RiskIQ, every endpoint connected to the internet faces 375 new threats per minute. Every 24 minutes, a new vulnerability is discovered.
Meanwhile, McAfee found that external attacks on cloud accounts have increased 630%, with transportation, government, and manufacturing most affected.
As attack attempts accelerate, organizations are shifting strategies.
While many companies have historically relied on VPNs to secure remote access, these solutions are also coming under scrutiny. With 500 known VPN vulnerabilities, many organizations are concerned these solutions may jeopardize IT’s ability to keep their environments secure.
While 93% of cybersecurity professionals currently leverage VPN services, 94% are aware that cybercriminals are targeting them to gain access to network resources.
In response, many organizations are adopting zero-trust security solutions, where users are continuously authenticated before being granted access to corporate resources. Various studies show that anywhere from 60% to 72% of organizations are working to implement zero-trust capabilities.
Still, data breach risks remain.
Research from WhiteHat Security and Forrester shows that 50% of apps have security vulnerabilities, and that 35% of external attacks in the past have been traced back to "buggy web applications."
As recently as 2019, less than half of small businesses were encrypting data or using two-factor authentication, and just 41% required strong passwords for access to mobile apps.
With the average business using anywhere from 102 to 288 different SaaS apps, and with 43% of data security breaches stemming from attacks on web apps, it’s becoming increasingly critical to vet vendors.
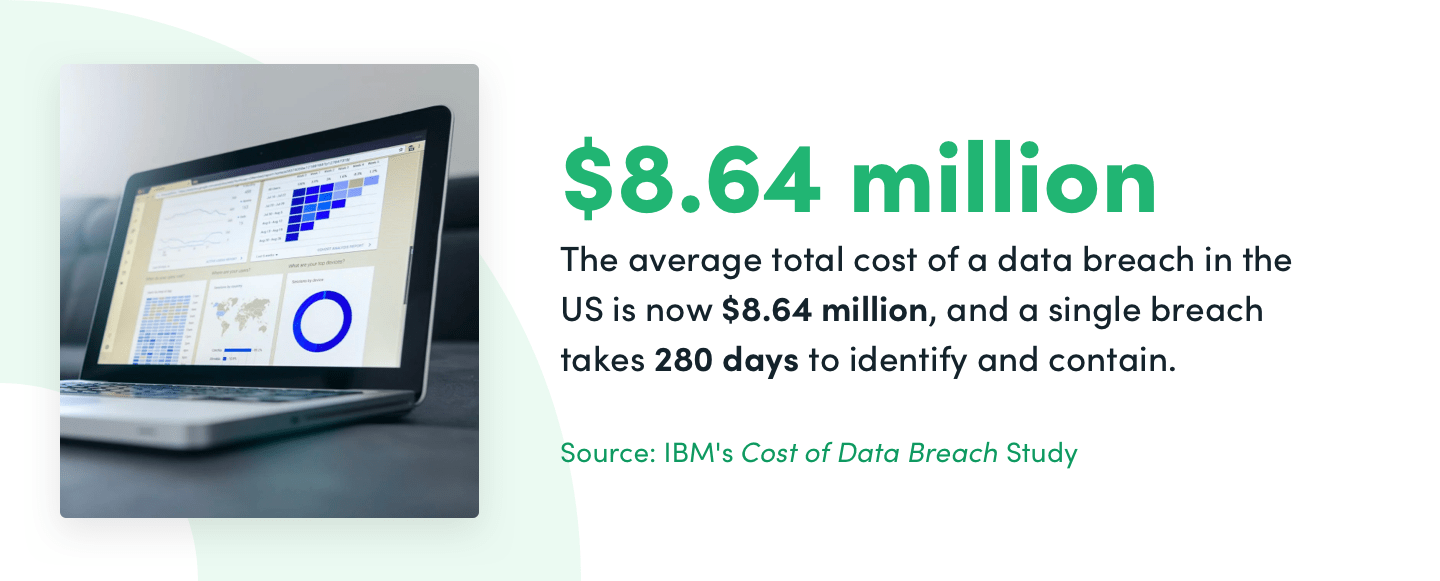
The average total cost of a data breach in the US is now $8.64 million, and a single breach takes 280 days to identify and contain. By comparison, the average cost savings of adopting a preventative solution to cyberattacks is just $800,000.
Related: Digital Transformation: How to Improve Data Security
It’s all leading to some serious IT strains
With so much at stake, it’s not surprising to see that escalating security concerns are driving budgets for 39% of surveyed IT professionals. According to The 2021 State of IT Report, 56% of those budgets are going toward updating outdated infrastructure this year.
That’s not all.
Research from INAP found that 59% of IT professionals are frustrated by the time they spend on routine infrastructure activities. Even more telling is the 84% who agree they “could bring more value to their organization if they spent less time on routine tasks.”
And then there’s the problem of too many tools. According to Gartner, cybersecurity operations are being complicated by the volume of vendors being used. Nearly 80% of CISOs have 16 or more tools in their cybersecurity vendor portfolio; 12% have 46 or more.
If these statistics sound scary, don’t panic. While the data-breach risks are real, there are plenty of emerging options that can be used to more easily identify, resolve, and prevent those threats—long before they become problems.
Did you know? The Formstack platform includes industry-leading security and compliance features to protect corporate resources. Visit the Trust Center to see how we help keep your data safe.